An additional feature has been added in Security Model with the 2015 release. This is an extension to the existing security model in which we use business units, security roles and teams. The hierarchy security offers a more access to records from an organization.
You can maintain the hierarchy with two different types of security model, one with the Manager hierarchy and another with the Position hierarchy.
In Manager hierarchy, a manager must be within the same business unit as the subordinate, or in the parent business unit of the subordinate’s business unit to easily access the subordinate’s records. Whereas in the Position hierarchy you can access data across the business unit.
Let’s explore how this actually works.
A new tile has been exclusively added for the security model which can been seen under the Settings area.
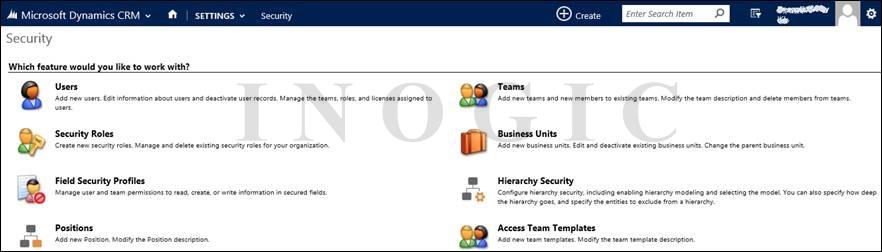
In this security tile you can find all the security related items added in it along with the “Positions” and “Hierarchy Security” which are two new items from Dynamics CRM 2015 release. You can enable the Hierarchy Security by following below steps:
- Open Hierarchy Security from the security tile:
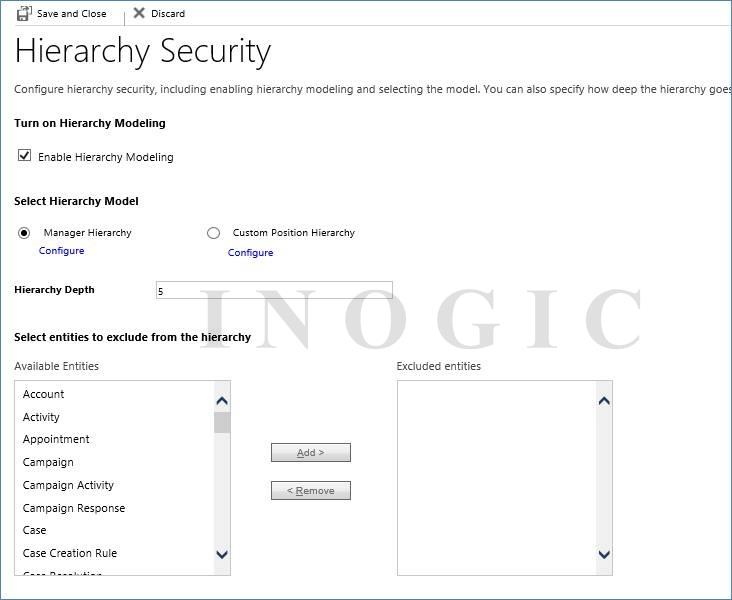
- Configure Hierarchy Security:
a. Turn on Hierarchy Modeling: A checkbox Enable Hierarchy Modeling will be used to enable or disable Hierarchy Model.
b. Select Hierarchy Model: Select whether you would like to enable Manager hierarchy or Position hierarchy.
A Manager hierarchy is based on the management chain where Manager and his/her subordinate’s hierarchy is set up. A User entity has a field Manager which will be used in this type of security model. Now the managers are able to access the data that their subordinates have access to.
A point to be noted in this model is a manager must have at least the user level Read privilege on an entity, to see the subordinate’s data. If a manager doesn’t have the Read access to the entity, the manager won’t be able to see the data of their subordinate.
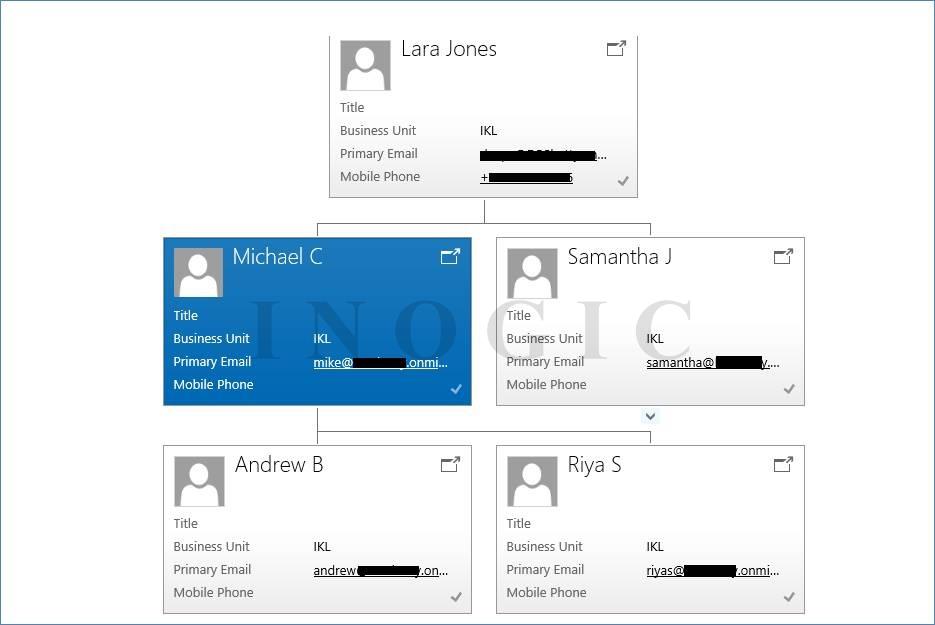
Position hierarchy is not based on the management chain structure like the Management Hierarchy. In this type of model a user doesn’t have to be a manager of another user to have access to the records. This hierarchy is based on the Position that has been defined in the organization. One the positions are defined arrange the positions and add users in the respective position. Now the user in the higher position can have access to the lower positions’ data.
c. Hierarchy Depth: Specify the Depth of the hierarchy to limit how many levels deep a manager has an access to the data of their subordinate.
d. Select Entities to Exclude from the Hierarchy :- You can select the entities which needs to be excluded from the Hierarchy Model.
- Setup Users according to the selected Hierarchy Model:
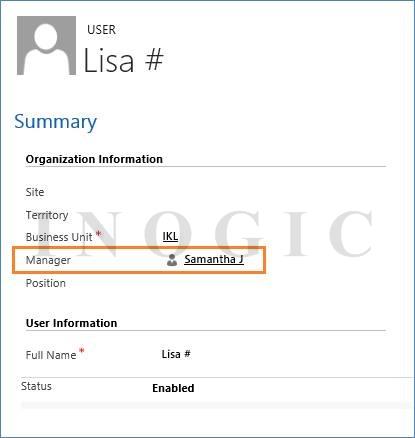
To setup Manager Hierarchy use the Manager (parentsystemuserid) lookup field to specify the manager of the user.
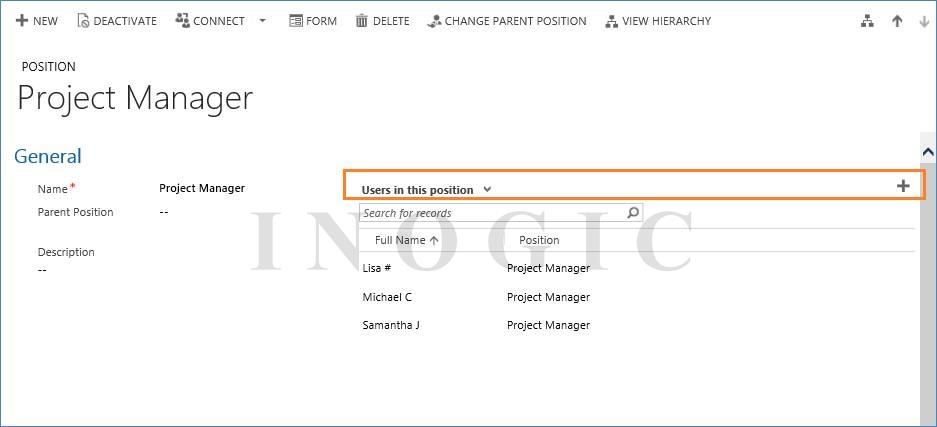
To create a position hierarchy you can create position with the Parent Position and description. After that, add users in the position by adding users in the grid “Users in this position”.
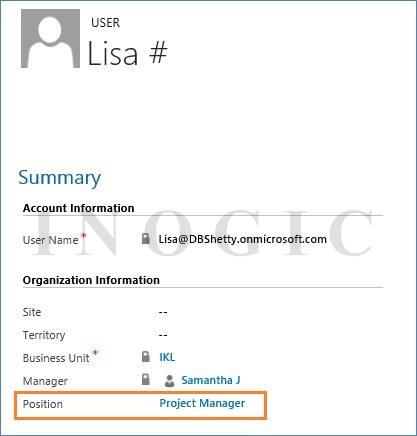
Or you can also use the lookup field called Position on the user record’s form, as shown below:
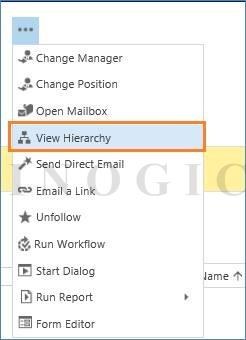
You can view the hierarchy by using button “View Hierarchy” which is visible in more commands.
Note that, hierarchy security model provides a certain level of access to data, if you want additional access then this can be obtained by using other forms of security, such as security roles.
With this new hierarchical data structure introduced in 2015 two new operators has also introduced to query data with this structure. The operators are Under and Not Under. Using these operators you can search for the records within the hierarchy. You can only see these operators for the entities which has self referential relationship (1:N) with it.
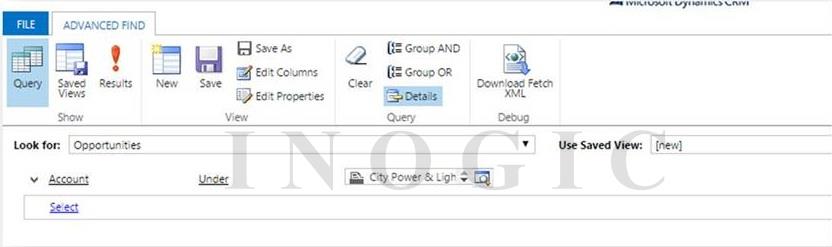
For Example: If you would like to see the opportunities under a particular account then you can query this hierarchy using UNDER operator. You can advance find with below condition:
So this will return the list opportunities under the selected account. Since we are querying the hierarchical data, if the selected account has its child accounts then the result will include those opportunities which belongs to the child accounts of the selected account.
Hope this helps!